A purchasing guide for Mobile Security – rich advisory on spend outlook in Mobile Security, pricing analysis for Mobile Security procurement cost benchmarking, negotiation strategies and key vendors of Mobile Security.
GET FREE SAMPLEEcosystem of the global Mobile Security category is intertwined with the larger parent market of Telecoms. Our category definition describes that overall Telecoms market includes all spend related to fixed and mobile telecoms including equipment and call charges, but excluding voice networks.
Business practices within Mobile Security market are heavily influenced by changing trends across the category as well as within the broader Telecoms market. Outsourcing of Mobile Security now represents a significant part of the global spend on this category, driven by value derived and a growing number of vendors who keep innovating with new services and value propositions. A balanced approach to procurement of Mobile Security has emerged, where buyers with multiple locations first outsource at individual locations and gradually move to standardize and consolidate the services across facilities. Suppliers have historically gained handsome margin-on-margin by sub-contracting a part of their work to another contractor. However, Buyers are now delving deep into the business models of suppliers and negotiating hard to avoid further sub-contracting. In cases where it is imperative to sub-contract, category managers are employing should-cost models to keep supplier margins on sub-contracting to the minimal. As a result, category managers need to closely monitor the Mobile Security procurement trends and identify changes required in their procurement environment for the category.
Mobile Security procurement best practices are moving towards a level of sophistication which is typically seen in traditional procurement categories. Category managers now have an attractive opportunity to adapt the best practices seen within this category as well as those being leveraged in other non-related categories. This report summarizes the best practices picked from across multiple categories that could work well for category managers involved with Mobile Security procurement strategy. For example, Buyers should set a baseline against which the performance of suppliers can be benchmarked along with setting measurable/quantifiable KPIs. Defined KPIs provides suppliers with clarity on the scope. Besides setting standards for operations, pricing, and performance, KPIs must provide tangible goals in terms of the quality of solutions. Category managers must explore opportunities to integrate planning and management activities of categories using analytics, to gain better control over category spend. This will also allow them to consolidate their supply base easily, as well as to segment suppliers based on requirements and spend on each supplier. Buyers must clearly define clauses pertaining to the ownership of sub-contracting services that are not a part of their preferred suppliers' portfolios. This will ensure consistency in the services of sub-contracted firms as well as protection of confidential data.
Activate your free account to gain easy access to cutting edge research and insights on consumers, emerging price trends, global and regional suppliers.
Mobile Security procurement managers also need to proactively identify and mitigate potential risks that can arise in the supply chain or contracts for Mobile Security procurement. Some examples include:
For detailed insights and complete access to our report library, activate your free account!
The report is intended to serve as a one-stop reference guide for Mobile Security procurement strategy and offers a perfect blend of category basics with deep-dive category data and insights. Therefore, it is ideal for category beginners looking for “Mobile Security: Procurement Report 101” as well as for category experts actively tracking the global Mobile Security procurement market.
You may have just initiated your research to design a winning Mobile Security procurement strategy, or you may be a category expert looking for strategic insights and updated data.Either ways, the report has your requirements covered.
Unlock SpendEdge's comprehensive procurement report collection with ease through our procurement platform.
Procurement decisions can prove to be costly in the absence of careful deliberation and evaluation of every available option. In fact, more than 90% of the decision makers we work with acknowledge that timely availability of up-to-date category intelligence can help them make better purchasing decisions. More than 80% of them believe that in-house category intelligence needs to be updated periodically to achieve full benefits. If you have read so far, we are quite sure you agree!!
The Mobile Security procurement report helps take more informed decisions by placing all the critical information and advice at the fingertips of a decision maker. It also specifically answers some of the key questions that we have been routinely asked during our industry outreach initiatives:
SpendEdge Insights has helped procurement professionals and sourcing teams manage multiple spend areas and achieve more than $2 billion in savings. Activate your free account today!
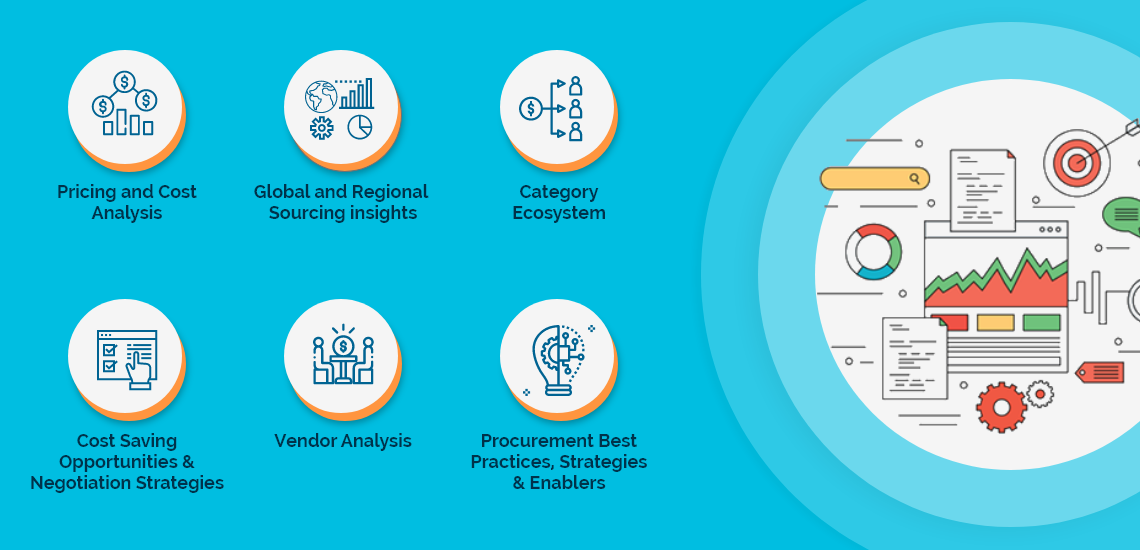
The Mobile Security market report offers a complete picture of the supply market and analyzes the category from the perspective of both buyers and suppliers. Analysis of the category trends, procurement best practices, negotiation levers and overall category management strategy advisory are interspersed with in-depth data and commentary on spend outlook, pricing ecosystem and supplier landscape drilled down to a region-level coverage.

A key highlight of this report is the in-depth outlook created on Mobile Security procurement spend and pricing trends. The report further delves deep into the aspects of cost structure, total cost of ownership and supplier margins for Mobile Security. A dedicated section to supplier profiles and evaluation helps decision makers cast a wider procurement net and identify gaps in existing relationships.

Along with specific category and supplier intelligence, the publication also includes curated insights on Mobile Security market trends, price influencers and inherent risks. These insights help the decision makers prepare for market shaping trends in advance and create alternative strategies for changes in the market conditions.

Additionally, the report also advises on the best practices and strategies to manage the Mobile Security category efficiently. Negotiation levers and opportunities are explained in detail along with quantification of their potential. Benchmark KPIs for supplier and buyer performance management are also aggregated to better organize the category objectives. Other themes of advisory include ideal procurement organization structure, enablers to achieve KPIs or category objectives and ideal SLAs to have with suppliers.






Our research is complex, but our reports are easy to digest. Quantitative analysis and exhaustive commentary is placed in an easy to read format that gives you an in-depth knowledge on the category without spending hours to figure out “what does it mean for my company?”
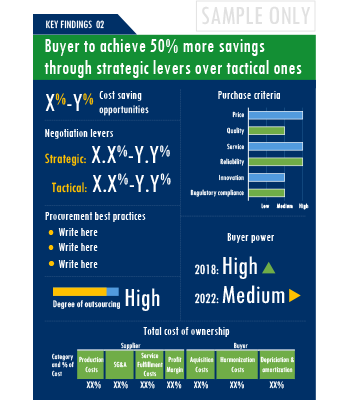
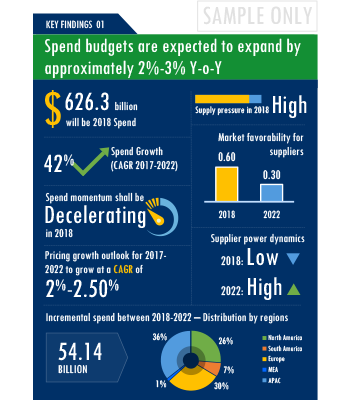
SpendEdge presents a detailed picture of Mobile Security procurement solutions by way of study, synthesis, and summation of data from multiple sources. The analysts have presented the various facets of the market with a particular focus on identifying the key category influencers. The data thus presented is comprehensive, reliable, and the result of extensive research, both primary and secondary.

Global Ngns Market - Procurement Intelligence Report

Global Payphones Market - Procurement Intelligence Report

Global Audio Conferencing Market - Procurement Intelligence Report

Global Cable and Satellite Television Services Market - Procurement Intelligence Report

Global ISDN (Integrated Services Digital Network) Services Market - Procurement Intelligence Report

Global Voice Carriers Market - Procurement Intelligence Report

Global Wireless / WLAN Access Services Market - Procurement Intelligence Report

Global Mobile Communications Services Market - Procurement Intelligence Report

Global Mobile Voice And Data Services Market - Procurement Intelligence Report
Access this report and our entire procurement platform | Plans starting from USD 3000/ Year Buy Now
Copyright © 2026 Infiniti Research Limited. All Rights Reserved. Privacy Notice – Terms of Use – Sales and Subscription
Cookie Policy
The Site uses cookies to record users' preferences in relation to the functionality of accessibility. We, our Affiliates, and our Vendors may store and access cookies on a device, and process personal data including unique identifiers sent by a device, to personalise content, tailor, and report on advertising and to analyse our traffic. By clicking “I’m fine with this”, you are allowing the use of these cookies. You may change your settings based on a legitimate interest at any time, by selecting “Manage Settings” on our site. Please refer to the help guide of your browser for further information on cookies, including how to disable them. Review our Privacy & Cookie Notice.