A purchasing guide for Security Software – rich advisory on spend outlook in Security Software, pricing analysis for Security Software procurement cost benchmarking, negotiation strategies and key vendors of Security Software.
GET FREE SAMPLEThis report on global Security Software category is part of a larger series of reports on global End User Software and Hardware market. The scope of End User Software and Hardware spans multiple categories and is typically identified as a procurement category that includes all spend relating to the provision of off the shelf software, computer equipment, components, upgradation and replacement.
The market for End User Software and Hardware and its sub-segments such as Security Software are at an interesting intersection. New locations and vendors are emerging as cost effective suppliers of Security Software, offering an opportunity to widen the supplier base and gain further negotiation leverage with incumbent suppliers.The ecosystem of Security Software is part of an industry which is developing a host of new transformative technologies. Billions of dollars are being invested into this industry, and companies are in cutthroat competition to discover the next game changing technology, hardware, software, and services.Stringency in the regulatory norms pertaining to data protection and cybersecurity has increased compliance and security burden on suppliers. These additional costs have a potential to drive marginal increase in prices across the key geographies.Trends like these and many others discussed in this report are necessitating a relook at the way Security Software is procured and the procurement cost saving opportunities that exist.
The report discusses in detail the best practices that have served well the category managers responsible for Security Software procurement. For example, Transferring to a new supplier can be often costly and can further get exacerbated by instances of vendor lock-ins. Buyers must scrutinize the offerings of service providers for any possibilities of vendor lock-ins and demand client testimonials from service providers to assess such possibilities. Watch out for products/services that are priced excessively low, as they can often result in costly lock-ins. Procurement functions should develop custom processes to gain better visibility and involve Security Software suppliers early in the procurement process. Prior to the commencement of contract-related discussions, buyers must ensure that they have clearly identified and listed down potential levers, such as duration of contract, resources required, space limits if relevant, terms of payment, expected resolution time, delivery point.
Activate your free account to gain easy access to cutting edge research and insights on consumers, emerging price trends, global and regional suppliers.
Security Software procurement managers also need to proactively identify and mitigate potential risks that can arise in the supply chain or contracts for Security Software procurement. Some examples include:
For detailed insights and complete access to our report library, activate your free account!
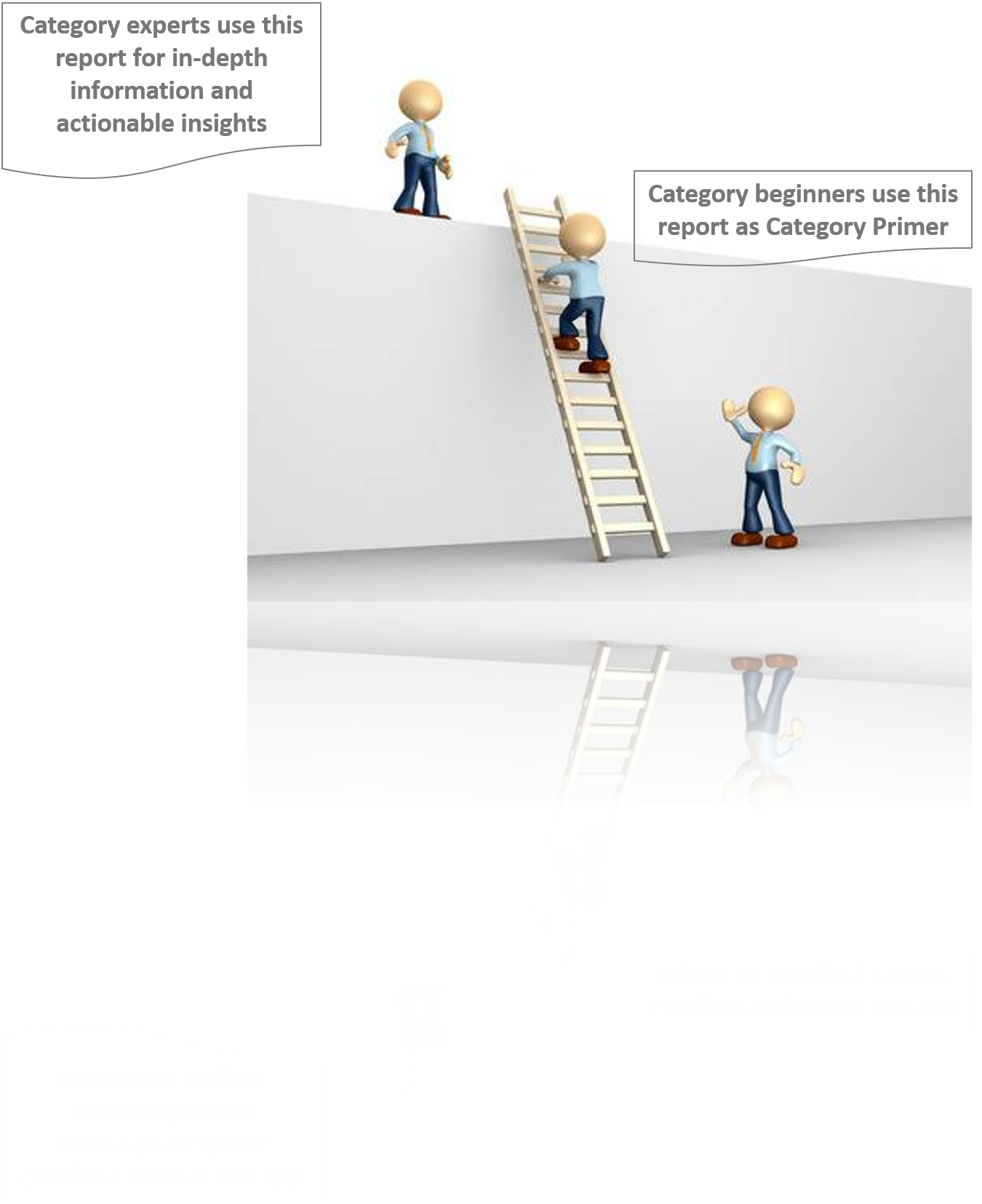
The report is intended to serve as a one-stop reference guide for Security Software procurement strategy and offers a perfect blend of category basics with deep-dive category data and insights. Therefore, it is ideal for category beginners looking for “Security Software: Procurement Report 101” as well as for category experts actively tracking the global Security Software procurement market.
You may have just initiated your research to design a winning Security Software procurement strategy, or you may be a category expert looking for strategic insights and updated data.Either ways, the report has your requirements covered.
Unlock SpendEdge's comprehensive procurement report collection with ease through our procurement platform.
Procurement decisions can prove to be costly in the absence of careful deliberation and evaluation of every available option. In fact, more than 90% of the decision makers we work with acknowledge that timely availability of up-to-date category intelligence can help them make better purchasing decisions. More than 80% of them believe that in-house category intelligence needs to be updated periodically to achieve full benefits. If you have read so far, we are quite sure you agree!!
The Security Software procurement report helps take more informed decisions by placing all the critical information and advice at the fingertips of a decision maker. It also specifically answers some of the key questions that we have been routinely asked during our industry outreach initiatives:
SpendEdge Insights has helped procurement professionals and sourcing teams manage multiple spend areas and achieve more than $2 billion in savings. Activate your free account today!
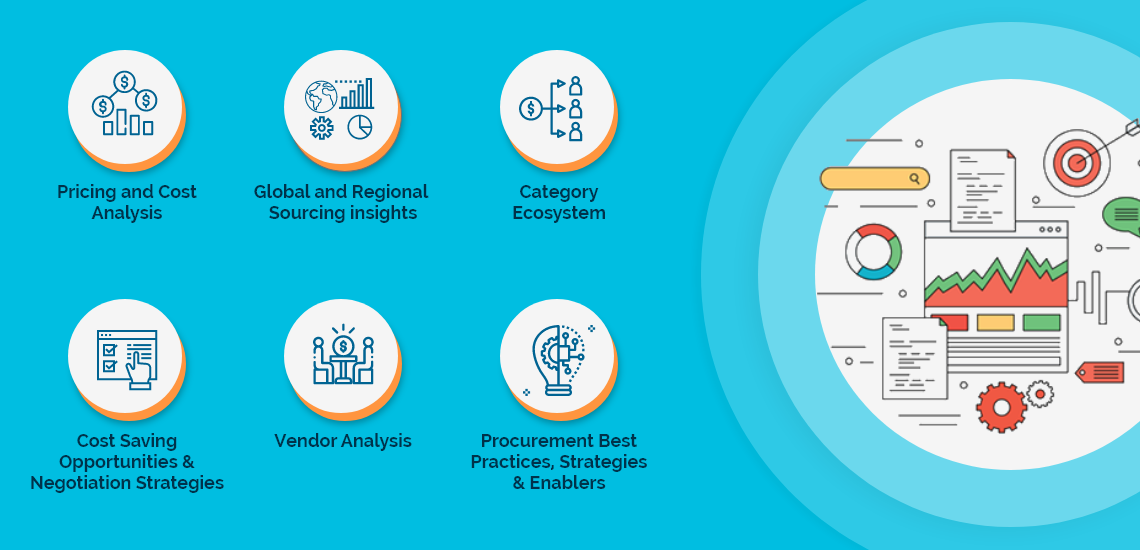
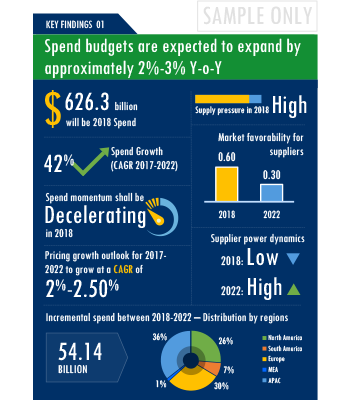
The Security Software market report offers a complete picture of the supply market and analyzes the category from the perspective of both buyers and suppliers. Analysis of the category trends, procurement best practices, negotiation levers and overall category management strategy advisory are interspersed with in-depth data and commentary on spend outlook, pricing ecosystem and supplier landscape drilled down to a region-level coverage.

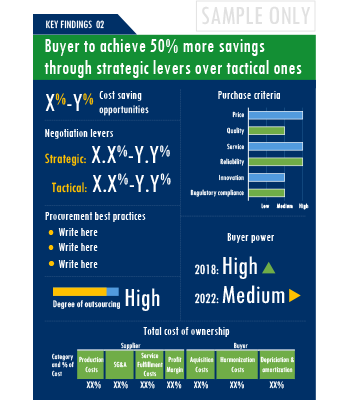
A key highlight of this report is the in-depth outlook created on Security Software procurement spend and pricing trends. The report further delves deep into the aspects of cost structure, total cost of ownership and supplier margins for Security Software. A dedicated section to supplier profiles and evaluation helps decision makers cast a wider procurement net and identify gaps in existing relationships.

Along with specific category and supplier intelligence, the publication also includes curated insights on Security Software market trends, price influencers and inherent risks. These insights help the decision makers prepare for market shaping trends in advance and create alternative strategies for changes in the market conditions.

Additionally, the report also advises on the best practices and strategies to manage the Security Software category efficiently. Negotiation levers and opportunities are explained in detail along with quantification of their potential. Benchmark KPIs for supplier and buyer performance management are also aggregated to better organize the category objectives. Other themes of advisory include ideal procurement organization structure, enablers to achieve KPIs or category objectives and ideal SLAs to have with suppliers.






Our research is complex, but our reports are easy to digest. Quantitative analysis and exhaustive commentary is placed in an easy to read format that gives you an in-depth knowledge on the category without spending hours to figure out “what does it mean for my company?”
SpendEdge presents a detailed picture of Security Software procurement solutions by way of study, synthesis, and summation of data from multiple sources. The analysts have presented the various facets of the market with a particular focus on identifying the key category influencers. The data thus presented is comprehensive, reliable, and the result of extensive research, both primary and secondary.

Global Digital Asset Management Software Market - Procurement Intelligence Report

Global Accounting Software Market - Procurement Intelligence Report

Global Field Service Management Software Market - Procurement Intelligence Report

Global Check Authorization Software Market - Procurement Intelligence Report

Global Virtual Data Room Software Market - Procurement Intelligence Report

Global ACA Compliance Software Market - Procurement Intelligence Report

Global Transportation Management Systems Market - Procurement Intelligence Report

Global E-Mail Marketing Software Market - Procurement Intelligence Report

Global Online Survey Software Market - Procurement Intelligence Report
Access this report and our entire procurement platform | Plans starting from USD 3000/ Year Buy Now
Copyright © 2026 Infiniti Research Limited. All Rights Reserved. Privacy Notice – Terms of Use – Sales and Subscription
Cookie Policy
The Site uses cookies to record users' preferences in relation to the functionality of accessibility. We, our Affiliates, and our Vendors may store and access cookies on a device, and process personal data including unique identifiers sent by a device, to personalise content, tailor, and report on advertising and to analyse our traffic. By clicking “I’m fine with this”, you are allowing the use of these cookies. You may change your settings based on a legitimate interest at any time, by selecting “Manage Settings” on our site. Please refer to the help guide of your browser for further information on cookies, including how to disable them. Review our Privacy & Cookie Notice.